Identity Management Systems (IdM) are often used to assign access authorisations for these systems, but often find it difficult to cope with the new challenges:
- Cloud providers are often not fully transparent and only allow access permissions to be granted indirectly.
- The abundance of new functions and applications increases the complexity of the approval processes and there is often a long delay before they can be implemented in the IdM.
- Avoiding and detecting access threats requires full visibility of users with authorisations that give them access to sensitive data as well as those with critical access combinations across the IT landscape. Its definition poses completely new challenges, both to decision-makers and the IdM system.
- The technical features of authorisations usually vary from system to system, leading to an increasing amount of work to assign and control authorisations. The combination of more new cloud systems and short deployment periods significantly raises the risk of access threats.
- Detecting threats from inappropriate access is difficult to identify.
SAP is keeping on top of this landscape with several innovations and new systems, including S/4 Applications and Database, SuccessFactors, Concur, Ariba, Fieldglass, Fiori and Cloud Application Lifecycle Management.
In addition, there are non-SAP systems, legacy SAP systems and SAP cloud architectures such as Hana Enterprise Cloud (HEC), all of which are relevant for identity management.
SAP meets the authorisation requirements with a wealth of new functionalities, some of which are still under development.
Access Governance
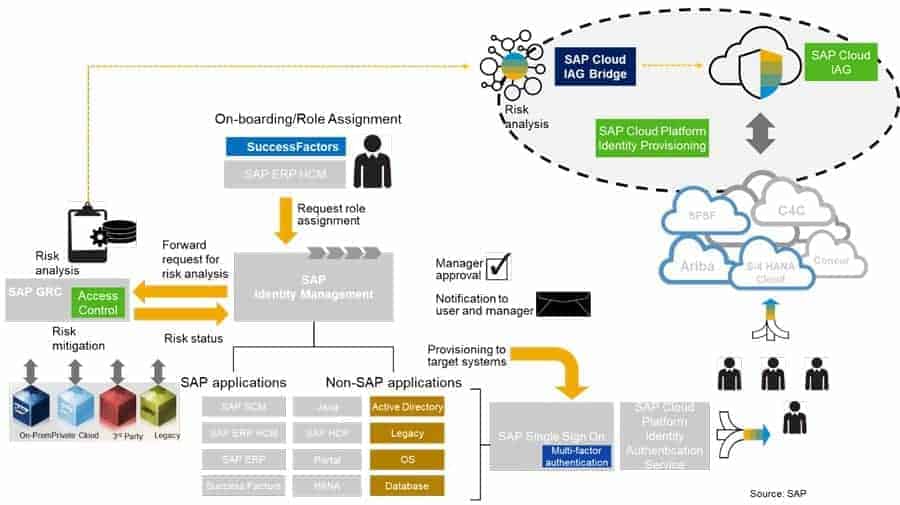
At the centre of the authorisation assignment features above are four essential Identity and Access Management systems:
- SAP Identity Management (IdM): used for on-premise SAP and non-SAP systems.
- SAP Cloud Identity and Access Governance (CIAG): this new application has been developed for cloud systems.
- SAP Access Control (GRC AC): Access Risk Analysis is primarily intended for risk management and access compliance as well as for risk mitigation. GRC AC also enables the development of authorisations for SAP ERP and S4/ systems. If IdM is not used, GRC AC is often adopted to assign authorisations for on-premise systems.
- SAP Single Sign-On (SSO) for logging on to on-premise systems.
The SAP Cloud IAG Bridge is an important part of the CIAG and enables the integration of on-premise and cloud access. In providing full visibility of user access across all systems, it is a key element for threat detection.
This transparency is necessary in order to analyse access risks correctly and comprehensively and to detect threats from users that don’t have appropriate access for their role. For example:
- Users that have assigned authorisations in a variety of systems that usually have their own specific technical authorisation concepts that follow their own access schema.
- Users that have access to personal data (that is potentially GDPR sensitive).
- Users with sensitive access and critical authorisation combinations.
The rules for risk analysis are maintained in GRC AC. The SAP Cloud IAG Bridge thus enables end-to-end risk analysis and risk reduction for the entire corporate IT environment, whether that is on-premise or cloud-based, SAP or non-SAP. The assigned authorisations over the entire user life cycle can therefore be reviewed with full visibility regarding their timeliness and adequacy: an essential requirement for management and audit.
Why a new Identity and Access System?
It’s reasonable to ask why SAP has introduced CIAG, another authorisation tool.
More and more organizations are adopting a ‘cloud first’ strategy, and a corresponding Identity and Access Governance platform is an obvious requirement; the assignment of authorisations for cloud systems requires different techniques and access threat detection methods than that of on-premise applications. For example, depending on the cloud strategy, third parties who require corresponding support processes are increasingly involved.
The road ahead
Currently, some important functions in CIAG are still under development. Availability of additional features can be monitored with a roadmap. More information about Cloud IAG can be found here.
Implementation of Identity and Access Governance
Anyone who has already implemented an IdM system whereby authorisation assignment must follow the usual principles of segregation of duties (SoD) can imagine the additional challenges that arise with cloud applications:
- The time from decision to deployment of cloud applications is often not long enough to develop an adequate user authorisation concept.
- Access approvers often do not have full visibility of the authorisation technology in cloud applications, which can often only be provided in basic form.
- Within a short period of time, many users must be authorised, often leading to extensive – and therefore excessive – access privileges being granted.
- The SoD risks and risk reduction features for the entire system landscape, including cloud-based systems, are unknown leading to a high risk of inappropriate and extensive user access.
- Cloud business processes are often not documented, nor do they indicate risks. As a result, additional analysis is required for critical process tasks such as approvals in access design projects. However, budgets are often not available for this and users are instead granted wide access, which increases risk.
‘Doing nothing’ is certainly not an option. To reduce the risk of threats from inappropriate access, it is necessary to analyse access risks. For critical system features, detailed authorisations can be defined. Broader access can be provisioned for less important features. The advantage of a risk-based approach is that the critical cloud functions and processes can be included within the combined SoD ruleset of GRC AC.
Summary
To avoid access threats, user specific authorisations that comply with general SoD principles have to be assigned. This requires an identity and access governance system that both highlights the risks of authorisations already allocated, and is able to process the different authorisation technologies of cloud applications.
With this article, Turnkey concludes its mini-series of articles, following their first one, that focuses on SAP Identity Management.






















Add Comment